In today’s blog, we’re kicking off our series on FIDO2 key authentication by exploring how to set up FIDO2 hardware key sign-in for Microsoft services. This secure, phishing-resistant multi-factor authentication (MFA) solution not only boosts security but also simplifies the login experience.
Table of Contents:
- Introduction
- Enable the FIDO2 Authentication method in Microsoft Entra
- Add the sign-in method for the user
- Test the FIDO2 key method using web logon
- Conclusion
1.Introduction
In this day and age protecting access to corporate resources is more crucial than ever. FIDO2 keys offer a simpler, more secure alternative to password-based authentication, eliminating the need for frequent password changes.
In this blog, we’ll guide you through setting up FIDO2 key authentication in Microsoft 365 and show how users can securely access their data.
Because let’s be honest, who hates changing their passwords every month? I know I do!
With a FIDO2 key , we can finally move to a passwordless future and ditch the hassle of remembering and updating passwords.
2. Enable the FIDO2 Authentication method in Microsoft Entra
Prerequisites:
At least an "Authentication Policy Administrator" role
A Microsoft certified Security key (we use the FIDO2 NFC Yubi Key)
Entra joined computers (for Windows Hello for Business)
First things first, before users can take advantage of FIDO2 key authentication you need to enable it as a supported sign-in method in Microsoft Entra.
Follow these steps to get started:
Steps to Enable FIDO2 Key Authentication in Microsoft Entra
- Open a browser and go to the Microsoft Entra Admin Center.
- Login with an admin account that has at least the Authentication Policy Administrator role.
- In the search bar, type in “auth methods”
- Select the “auth methods” service

Configure the passkey method
In the list of authentication methods, locate “Passkey (FIDO2)”.
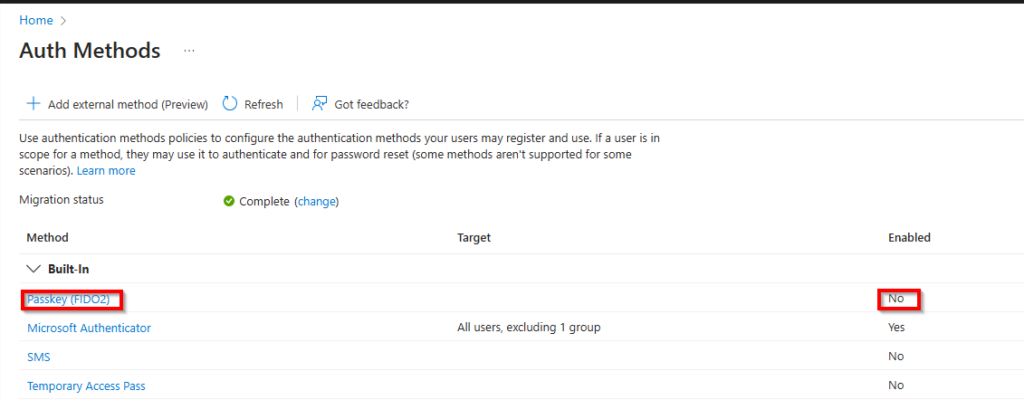
As you can see, the method isn’t enabled yet and needs to be configured. Click on it to start the process.
I recommend starting with a test user group. Once you're confident everything is set up correctly, you can either keep the current group, switch to another group or enable this method for all users.

Now we need to configure the policy, follow:
- Enable the Policy
- Toggle the policy to Enabled.
- Select the Target
Choose whether to apply the policy to all users or specific groups. - Add Groups (If Applicable)
- If you selected the group option, click Add groups, choose your desired groups, and click Configure.
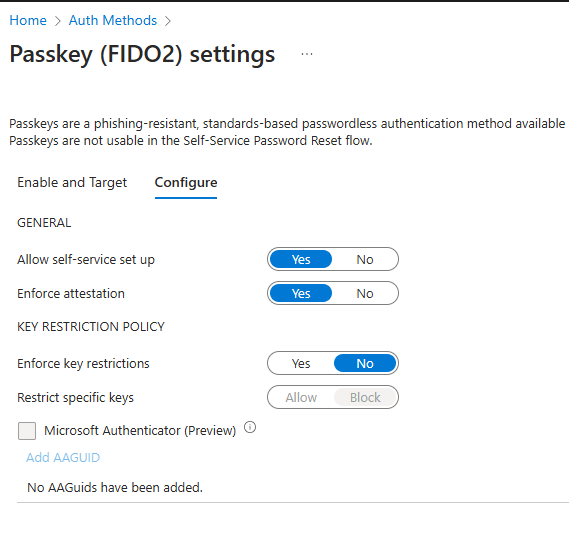
These are the settings I used for this scenario. If this is your first time setting up FIDO2 keys, I wouldn’t recommend enabling key restrictions just yet. There are tools available to identify the AAGUID on your FIDO2 keys, but let’s keep things simple for now.
Once you’ve configured the settings to your liking, click Save to enable the FIDO2 key authentication method.

As you can see, the policy is now enabled. This means you can now add this authentication method to a user, allowing them to start using the security key for authentication/passwordless sign-ins.
It can take between 5-45 minutes before the method is available to use. If it doesn't work right away don't panic, it will eventually be available to you.
3.Add the sign-in method for the user
After enabling the FIDO2 authentication method and configuring the security key as a sign-in option for Windows Hello for Business (which we’ll cover in a future blog), the next step is to assign this method to a user who is a member of the FIDO2 Token Group we specified earlier.
Here are the steps to add the sign-in method to a user:
- Go to the My Sign-Ins Portal and add sign-in method
- Navigate to My Sign-Ins.
- Sign in with your Microsoft account.
- Once signed in, click on “Add method” at the top of the page.
- Select Security Key as the Method
- From the dropdown menu, select “Security key”.

3. Choose the Key Type
- Select the type of security key you are using:
- USB Device: For keys that connect via USB.
- NFC Device: For keys that connect wirelessly using NFC.
- Our key has both capabilities but we will choose USB device for now.

4. You’ll be prompted to insert the key into the USB port. Once the key is inserted, click Next to begin the pairing process.

You will now be redirected to a new page to set up the passkey.

5. Next, choose where you want to save the key. Select Security key and click Next.
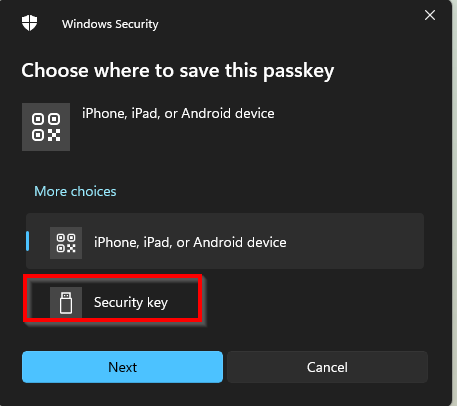
6. You’ll see a couple of confirmation screens from Windows Security. Click OK twice to continue.


7. If you have a new key (and I assume you do), you’ll need to create a PIN for it. Enter a new pin code twice and click OK.

8. This is where the key truly excels. You’ll be prompted to touch the security key. The Y indicator will turn green, signaling that you need to touch it. This adds an extra layer of security, as only someone with physical access to the key can complete this step—making it hacker-proof.




We’re all set! You’ll be asked to give your FIDO2 key a name and to save it.

The authentication method has been successfully added and can now be used across all Microsoft services/
Your preferred authentication method has also been updated to FIDO2, as it offers a more secure option than the Microsoft Authenticator.
4.Test the FIDO2 key method using web logon
Below are the step to test the Fido2 key sign-in method on the Microsoft portal.
- Go to a Microsoft Portal page
- Select Sign-in options

3. Select the Security key option

4. Select Different Passkey if the system detects a previously saved key, such as a Windows Hello for Business key.

5. Select the security key option

6. If you’re prompted with other options instead of the key, select Use another device and choose Security key, then click Next.

7. Enter your security pin and touch the key to continue.


You’ve now successfully completed your first passwordless sign-in!
5. Conclusion
In conclusion, FIDO2 hardware key sign-in provides a secure, phishing-resistant authentication method while offering a passwordless login option. It enhances security and improves user experience by eliminating the need for complex passwords. Microsoft now recommends against password expiration, as users often forget them or write them down, which can undermine security.
This marks a shift from past practices where expired passwords were seen as more secure and you got extra security score point for it!
In the upcoming parts of this blog series, we’ll dive into configuring Windows Hello for Business to use FIDO2 keys, including how to sign in with this method on mobile devices. Additionally, we’ll explore how to use the FIDO2 key for secure Privileged Identity Management (PIM) role activation. Since this topic is quite detailed and long , we’ve divided it into a three-part series to provide a thorough understanding of each aspect. Stay tuned for part two and three!