To my surprise, I haven’t written about Intune yet.
Given that my header promises content about Intune, it’s about time we dive into this topic!
Today’s blog will be about enhancing security and streamlining the management of local administrator passwords across your Windows devices by implementing LAPS with Intune.
In this article, we’ll walk you through the step-by-step process of setting up LAPS with Intune and explore the numerous benefits it can bring to your organization. Whether you’re looking to improve your security or simplify password management, this guide will provide you with everything you need to get started.
Table of Contents:
Prerequisites
Understanding LAPS and its Integration with Intune
Step-by-Step Guide
Step 1: Enable LAPS in Microsoft Entra
Step 2: Enable the local admin account
Step 3: Create the LAPS policy in Intune
Step 4: Test the solution
Troubleshooting
Final Thoughts
Prerequisites
Setting up Local Administrator Password Solution (LAPS) for your Intune tenant for the first time is straightforward, but it does come with specific requirements (I know because I didn’t meet them in my first test 😅).
To ensure Intune supports Windows LAPS in your environment, you’ll need to meet the following prerequisites:
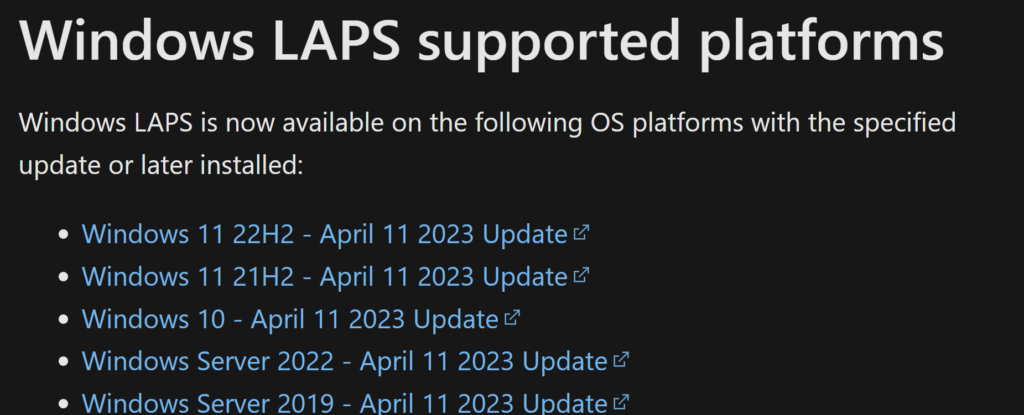
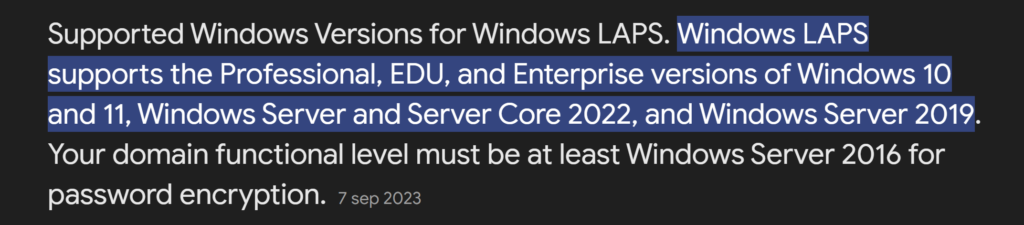
Windows OS requirements:
License requirements:
Microsoft plan with at least:
- Microsoft Entra ID
- Intune Plan 1
Most companies have above licenses and the required Windows OS so it shouldn't be a problem for them to use LAPS.
Understanding LAPS and its Integration with Intune
Local Administrator Password Solution (LAPS) is a Microsoft tool designed to improve the security of local admin passwords on Windows devices. By generating unique passwords for each device and securely storing them on-premises (Active Directory) or in the Cloud (in Entra ID), LAPS addresses the security risks of shared, old and unsecure passwords (or passwords that never get changed even if staff changes happen the password are the same for many years!).
When combined with Microsoft Intune, LAPS provides a centralized way to manage these passwords, enhancing security and simplifying administrative tasks. Here are the key advantages of using LAPS with Intune:
- Centralized Oversight: Intune streamlines the management of admin passwords across all Windows devices from a single platform.
- Enhanced Security: Unique and complex passwords for each device reduce the chances of unauthorized access.
- Built-In Functionality: The latest Windows OS versions come with the LAPS agent, removing the need for additional installations.
- Operational Efficiency: Automating password updates frees up time and resources that would be spent on manual changes.
- Compliance and Monitoring: LAPS offers a detailed audit log of password changes, ensuring adherence to security policies and facilitating easy monitoring through Intune.
Using LAPS with Intune not only boosts your security framework but also simplifies the management of local admin passwords, making your IT processes more efficient and secure.
Step by step guide
In this section, we will walk you through the process of setting up LAPS with Intune. Follow these steps to ensure a smooth and successful implementation of Local Administrator Password Solution in your environment. Let’s get started!
Step 1: Enable LAPS in Microsoft Entra
The initial step is to activate the LAPS solution through the Microsoft Entra ID portal. Follow these steps to verify if LAPS is already enabled or to enable it:

After activating the LAPS solution, it’s important to enable the default built-in local admin account. Windows disables this account by default for security reasons, but we will use this account for the LAPS solution (You can use another account if you prefer).
Step 2: Enable the local admin account
We need to create a new device profile.
First Navigate to the Intune portal and go to Devices -> Configurations.
Press Create and select New policy. Select Windows 10 and later as the platform and pick the Settings catalog as the profile type.

Name your policy and press Next.

In the configuration settings page, click Add settings and select the policy.
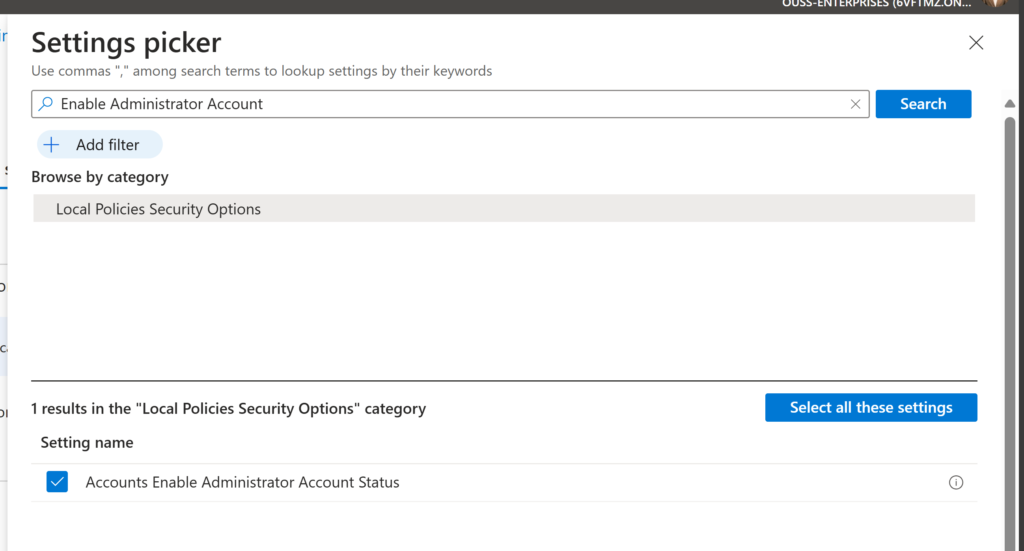
Enable the policy and press next
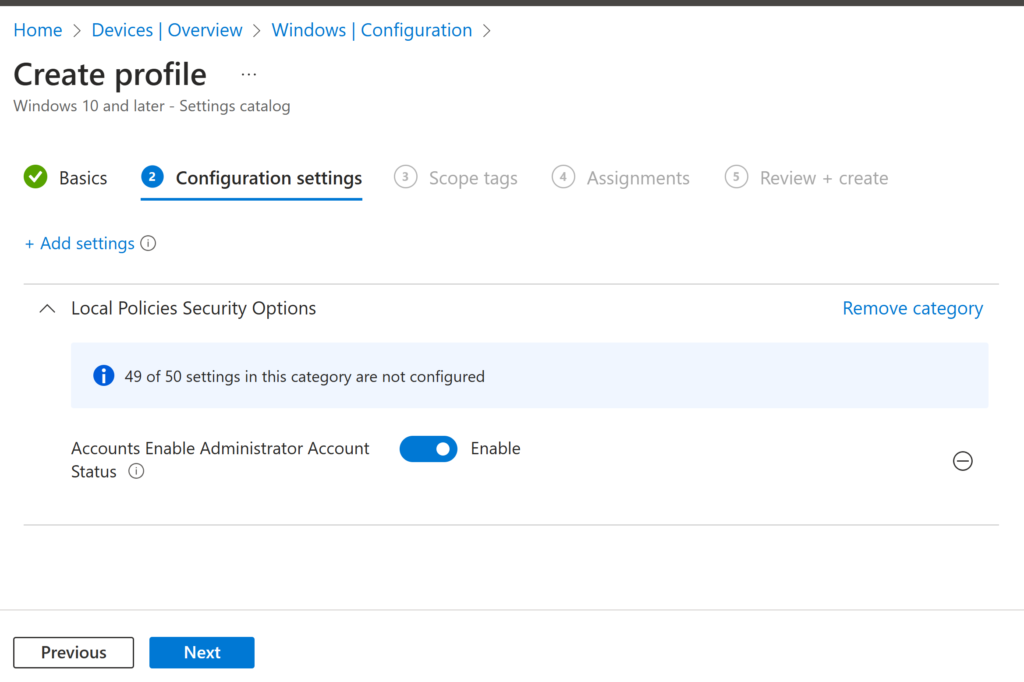
Configure scope tags or special assignments if needed.
We opted to enable the policy on all devices, ensuring that the policy applies universally (We don’t recommend using user assignment!).

Review the policy and click Create.
Now that we have enabled the local admin account we need to create the LAPS policy.
Step 3: Create the LAPS policy in Intune
In this step, we will create the LAPS policy in Intune and push it to all devices.
From the Intune Portal, go to Endpoint security -> Account protection. Click Create Policy and select Windows 10 or later and Local admin password solution (LAPS).

Give your profile a name and click Next. Configure the settings you want to apply.. Below are the settings we configured:
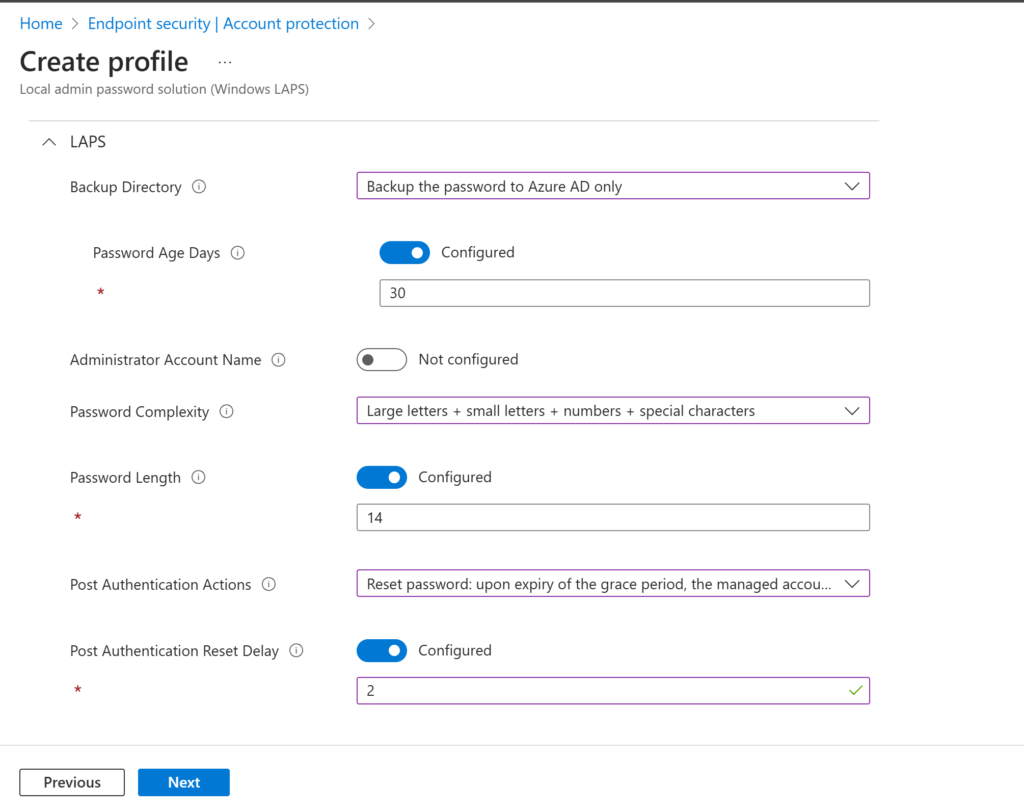
If needed, configure scope tags or special assignments. We want to enable this policy on all devices so select All Devices (If you want to exclude devices you can configure that on this step as well).

Review the settings and click Create.
After a few hours, the devices will pick up this setting.
To speed up the process, you can manually sync the device:

or bulk sync multiple devices.

Step 4: Test the solution
After waiting for a little bit you could check if the policy have been applied to your device by checking the overview page of the created LAPS policies:
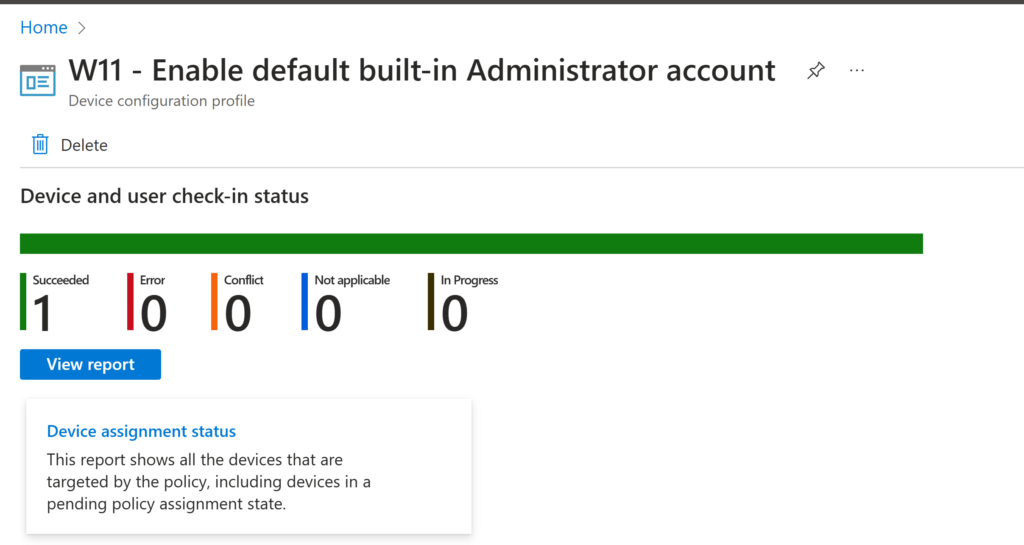

As you can see the policies have been applied successfully. We will now test the laps solution to see if it works.
Go to the Intune portal and select the device you want to test with. Click Local admin password -> Show local admin password and Copy or view the password from there.

Use the LAPS-generated password to start a process that requires administrator credentials.

If you can open the elevated command prompt succesfully, the LAPS solution has been implemented correctly!
If the solution doesn’t seem to apply or work, check the following part.
Troubleshooting
If you’re experiencing delays in the policy applying, you might want to check the following on the device:
Registry
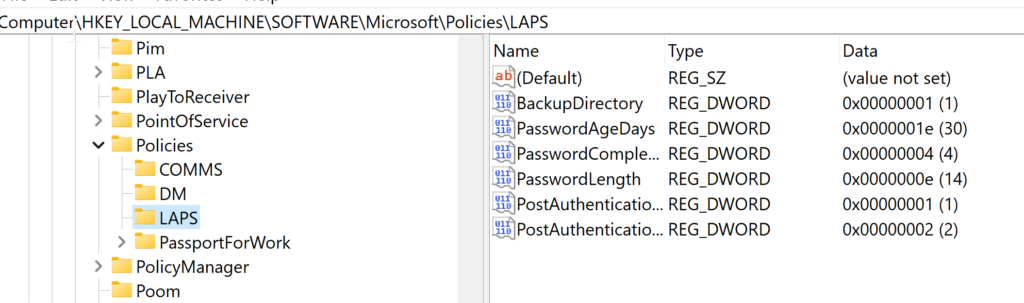
Verify that there is a new registry entry for LAPS with the applied settings. If the entry is missing, LAPS might not be functioning correctly, and you may need to update the OS. (This was the case for me with an outdated VM🙄). The oath should be:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Policies\LAPS
Event viewer
You can also check the Event Viewer for any issues. Look for a new LAPS folder created under the following path:
Application and Services Logs -> Microsoft-Windows-LAPS/Operational
Final Thoughts
Implementing LAPS with Intune boosts your security by automating local admin password management and fixing issues like outdated or unsafe practices.
This makes your admin tasks easier and keeps your IT environment compliant and efficient.
I hope you enjoyed this in-depth and technical blog post. I aim to balance content for various audiences, so you’ll see a mix of detailed guides and practical tips. Your feedback helps me fine-tune this balance, so feel free to share your thoughts!
Untill next time 💪